A month ago, I had the privilege of diving deep into the world of fraud detection in the telecommunications industry, thanks to a meeting with one of our esteemed clients. It wasn't just any meeting; it was a revelatory experience that reshaped my understanding of the intricacies and challenges of fraud detection. The insights I gained were so profound and transformative that I felt an irresistible urge to share them with you.

The telecommunications industry is often seen as a bastion of innovation and modernity, and yet only a few people are aware of the dangers that plague this sector: fraud and scams. Contrary to the popular belief that the banking sector is the main target for fraudsters, the telecom industry is just as intensely involved in this problem on a daily basis. Confirmation of this can be found in an article by the Communications Fraud Control Association, which estimated that fraud in the telecom industry alone has increased by 12% in 2023, reaching almost $39 billion! This is equivalent to 2.5% of telecommunications revenue.
Surprising? The numbers don’t lie, but telecommunications, like the finance and banking industry, is an arena of constant battle against fraudsters. It's not just about sophisticated cyber-attacks, but also something much more complex, and something that is highly specific and unique to this industry, but we'll get to that in a moment.
With billions lost to fraud every year, the impact of scams on telecom companies is not just significant, it is staggering. It goes beyond financial losses; perhaps more importantly, it erodes customer confidence and undermines the integrity of telecom services. Tackling this pervasive problem requires immediate action and a dedicated strategy to protect against these threats, ensuring the sustainability and security of the telecom sector in the face of ever-evolving fraud tactics.
This article is just a gateway, a starting point into the vast and shadowy realm of the Telecom Fraud World. It outlines various fraudster profiles without delving into the technical complexities. Going forward, detailed descriptions and examples of Nussknacker’s solutions for each type of fraud will be covered in separate articles.
Interconnect Frauds
The Interconnect is arguably the most crucial factor when it comes to fraud in telecommunications. It’s worth bearing in mind as it's almost always the starting point for most frauds.
What exactly is this Interconnect? It's the termination rate for a single SMS / MMS or call time between operators that is regulated by law. Operators also settle data transfers among themselves. Each country has its own regulator and regulations; e.g. in Poland there is the UKE and rates between domestic operators are symmetrical (you can find current rates here). On the other hand, rates between international operators are set individually, and the level of these rates depends not only on the statistics of telecom operators, but also on several other factors, such as the geographical distance between the telecom countries involved. This complex system highlights the nuanced relationship between distance, connectivity and the financial dynamics at play in setting international telecoms’ rates.
Mobile Transfer Rate
MTR – the charge that a mobile network operator receives from another operator for terminating calls to numbers on their network.
Fixed Transfer Rate
FTR – the charge that a fixed network operator receives from another operator for terminating calls to numbers on their network.
How does the operational interconnect mechanism work in real life? Let’s imagine a scenario in which User A, a customer with Telecom operator A, calls or sends an SMS / MMS to User B, a Telecom operator B customer. In this case, it is the responsibility of Provider A to pay Provider B a pre-determined and mutually agreed upon fee for the handling and seamless execution of this telecommunications service.

So the call initiator's carrier pays for the call. At first glance, it looks perfectly clear and there's no room for fraud. From the telecom's point of view, they just have to cover all fees related to the traffic that they control.
Artificial traffic
And yet nothing could be further from the truth. Let’s imagine that a fraudster creates fake traffic (calls / sms / mms) in order to charge operators for services handled? Clearly, there is a potential for fraud here.
The problem gets even trickier because telecom companies allow other private companies to set up their own mini telecommunication companies or create virtual operators that can use their infrastructure and so on. In addition to the problems with operators, there are also issues with premium rate numbers (with additional high charges). This scenario is playing out with alarming regularity, and the task of monitoring international traffic is becoming increasingly difficult due to the differing objectives of the various entities involved. Occasionally, these organisations may even be complicit in the perpetration of fraud. In the unfortunate event that a company finds itself defrauded, the burden of proof is on the company to prove the fraud; a task that is rarely easy. This multifaceted problem not only emphasises the pervasive risk of fraud within the industry but also highlights the urgent need for more robust monitoring and verification processes to mitigate these vulnerabilities.
Frauds within the realm of Interconnect traffic include, but are not limited to:
- WANGIRI Classic: A scam where victims receive a missed call from an international number, enticing them to call back, often resulting in charges to premium rates.
- INBOUND Wangiri: Similar to WANGIRI Classic but specifically targeting inbound calls to trick victims into incurring high charges.
- INBOUND Roamers: A variation that manipulates call routing to create scenarios where incoming calls result in exorbitant charges for the receiver.
- SIM Boxing: The use of illegal devices (SIM boxes) to reroute international calls as local ones, bypassing official network tariffs.
- SMS Artificially Inflated Traffic: Unsolicited messages sent in bulk to numerous recipients in order to generate fake traffic and often for advertising or phishing.
- IRFS (International Revenue Share Fraud): A scheme where fraudsters generate calls to numbers with high call rates, sharing profits with the number's owner.
- PBX Hacking: Unauthorised access to a company's private branch exchange (telephone system), leading to fraudulent calls at the company's expense.
According to the GLF Frauds Report from 2023, the proportion of carriers identifying fraudulent traffic as a 'top' or 'strategic' priority has soared to 92%, an unprecedented level and a significant increase from 77% in 2022. These figures demonstrate the seriousness of the threat to the telecom industry and highlight the importance of continued vigilance and sophisticated security measures.
Telecom Credit Frauds
Extortion of a fake customer’s financial capacity to buy an expensive device (such as the latest iPhone) as part of a telecom subscription is a typical form of fraud used by criminals looking for loopholes in credit verification systems.
Building a false capacity
The process often starts by setting up a non-existent company or using a company that, at first glance, appears to be operating a legitimate business. Then, to build up a positive credit history, the fraudsters pay low subscription fees or other small financial commitments for a set period of time – often a year or two. This creates the appearance of solid financial standing in the eyes of financial institutions or service providers, such as telecom operators. Once the false creditworthiness has been sufficiently 'documented', fraudsters can then apply for expensive subscriptions with equipment or other forms of financing that they cannot actually afford. After gaining access to expensive equipment or financing, they disappear, leaving behind debts and unpaid obligations.
Identity theft
Another type of credit mining is identity theft, which is when someone secretly pretends to be you and uses your name and personal information to get phones or services. It's like someone sneaking into your life, wearing it like a badge, and causing trouble without your knowledge. In the end, the thief with the false identity tries to get credit for the service or device.
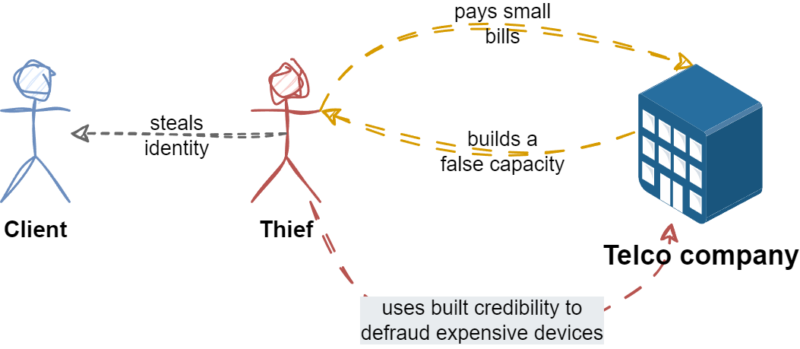
Such actions not only cause losses to the companies and institutions that have been defrauded, but can also have a negative impact on the market, raising the price of services for honest consumers and making access to credit more difficult for others. The CFCA Fraud Survey revealed that equipment and service fraud accounted for approximately 6% of all fraud committed in 2023.
Telecom Phishing & Spoofing
Last but not least, I'd even say it's one of the most common scams these days! Phishing & Spoofing are used together in the telecom industry and pose a serious threat to users' security and privacy.
These involve fraudsters sending fake SMS or MMS messages to trick recipients into sending sensitive information such as personal details, credit card numbers or passwords. This kind of message often contains links to suspicious websites that attempt to simulate legitimate sites or take over control of our device. Most of the time, the simulations are impressively realistic and are virtually identical to the legitimate source.
These malicious activities can range from fake security alerts to messages from purported financial institutions or well-known brands, even from the government. So you can probably see by now the seriousness of the threat.
The operational disruptions caused by responding to and mitigating the effects of phishing attacks also divert resources from innovation and growth. Fighting phishing is therefore not only about preventing financial loss, but also about maintaining the integrity of telecommunications services and the trust of the consumers who rely on them.
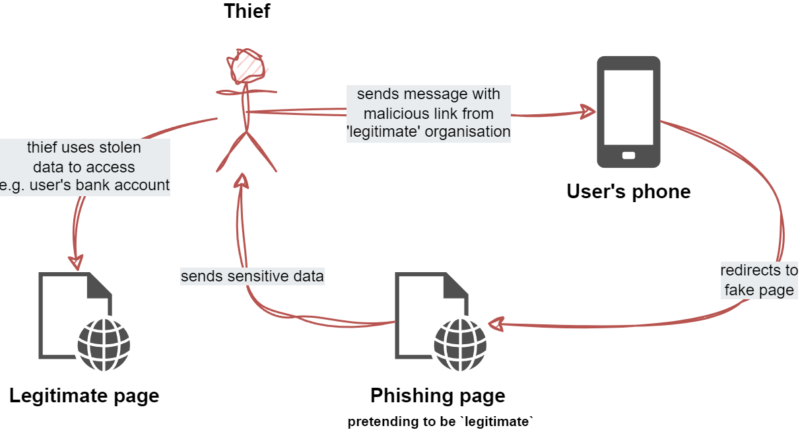
According to the GLF Report, the proportion of operators witnessing a rise in messaging fraud has nearly doubled from 2022 to 2023, jumping from 35% to 61%!
To get more information about this particular fraud and how to deal with it, check out our article Nussknacker Phishing & Spoofing Solutions!
Summary
According to reputable organisations such as the GSMA (Global System for Mobile Communications Association), CFCA (Communications Fraud Control Association), GLF (Global Leader Forum), MEF Forum and i3Forum, fraud in the telecom industry is a significant and growing problem. These organisations highlight that this kind of fraud poses substantial challenges to the sector. Year after year, the problem is escalating, becoming increasingly sophisticated and widespread, and affects both providers and consumers alike. Despite the alarming increase in fraudulent activity, there's a disturbing trend among companies in the industry. Many of them are prioritising the development and launch of new services over implementing measures to mitigate fraud losses. This focus on expansion over security can leave companies and their customers more vulnerable to fraud, emphasising the need for a balanced approach that includes robust fraud prevention strategies alongside growth initiatives.
Fraud Management Systems & Tools
If you look at the CFCA Fraud Loss Survey, it's clear that fraud prevention departments are now consistently using automated systems to detect fraudulent activity. Technology has become an integral part of their daily efforts to combat fraudsters. We believe that Nussknacker can be one of these systems. Battle-tested over five years within Play, one of Poland's largest telecommunications companies, Nussknacker provides 70 scenarios for fraud detection and problematic usage patterns, saving the company millions and protecting their customers. Check out our case study!
→ Want to learn more about telecom fraud? Go to the next post in the series: SMS artificially inflated traffic.
→ follow the author: Łukasz Ciołecki