
Real-time transaction fraud detection

Fraud prevention introduction
This article explores the importance and challenges of real-time fraud detection and how advanced technologies are enabling organisations to effectively combat fraud. The concepts discussed here align with the insights presented on our Nussknacker YouTube Channel, where we explore how real-time transaction processing is transforming fraud prevention.
But theory alone is not enough, real-world application is key. That’s why we invite you to explore our interactive demo, where you can see our fraud detection example in action. This hands-on experience allows you to visualise how transactions are processed in real time, how fraud patterns are detected, and how flagged transactions are handled efficiently.
Why is detecting fraud in real time so important?
The number of online transactions has skyrocketed in recent years, making it increasingly difficult for businesses to monitor and verify each one effectively. Alongside this growth, fraud attempts have escalated, putting merchants and payment providers at greater risk. Legacy fraud detection systems, which rely on delayed batch processing, are no longer sufficient in preventing evolving threats. To effectively counteract these risks, businesses must implement real-time fraud detection, allowing them to swiftly identify and block fraudulent activities before they result in financial losses.
Fraud detection challenges in real-time
Real-time fraud detection is complex because it requires analyzing vast amounts of transaction data instantly while distinguishing between legitimate and fraudulent activities. Fraudsters continuously adapt their tactics, making it difficult to rely on fixed rules or historical patterns.
Fraud detection systems in real-time must meet several requirements, which are difficult to meet in isolation and even more difficult to meet together:
- low latency: must process massive data streams instantly to prevent transaction delays,
- high accuracy, requires advanced AI and machine learning models to minimize false positives and false negatives,
- scalability: should handle high transaction volumes without performance degradation,
- fault tolerance: must ensure uninterrupted operation even during system failures or peak loads,
- complex architecture management: typically consists of multiple technologies for data collection, transformation, detection, and alerting, making integration and maintenance challenging,
- specialized expertise: requires skilled professionals to build, optimize, and maintain complex fraud detection models and infrastructure,
- cost efficiency: requires significant investment in infrastructure and technology while maintaining affordability.
Simplifying real-time fraud detection with Nussknacker
Nussknacker makes real-time data processing more accessible by providing a low-code platform with an intuitive drag-and-drop interface, allowing businesses to build and manage fraud detection scenarios without deep technical expertise. Powered by stream processing with Low-code Apache Kafka and the engine based on GUI Apache Flink, it ensures high-speed data processing with windowing & aggregation, all of these with minimal latency.
Besides real-time streaming, Nussknacker also utilizes batch and synchronous data processing. It enables seamless integration of multiple data sources, allowing users to ingest and enrich transaction data, define fraud detection rules, and apply machine learning models for intelligent threat prevention - all in one scalable and fault-tolerant system.
Real-time fraud detection solution
A financial provider or bank publishes all transactions onto an Apache Kafka topic, allowing for real-time processing. At the core of our fraud detection system is Nussknacker, which handles these transactions in a stateful manner, applying detection rules. Here, stateful means that transactions are correlated with other transactions, typically based on the customerId or card number. The fraud detection algorithms take into account also these correlated transactions. The correlation occurs in the engine memory and therefore is much faster than using traditional database-based solutions. As an output, the system generates a new Kafka stream, this time with flagged fraudulent transactions, enabling swift action to prevent financial losses.
Each transaction follows a specific format, including key details such:
- transactionId: String
- amount: Decimal
- clientId: String
- latitude: Double
- longitude: Double
- eventDate: Long
How to configure Kafka with Nussknacker can be found in our documentation.
Suspicious transaction cases
With Nussknacker, there’s no need for complex code or SQL queries to detect fraud. You don’t have to manage multiple processes or separate workflows, everything can be handled within a single graphical scenario. Its intuitive drag-and-drop interface allows you to define fraud detection rules, process transactions in real-time, and apply *machine learning models seamlessly, all in one unified environment.
*In this example we don’t use machine learning models, you can read more about Nussknacker’s ML related features.
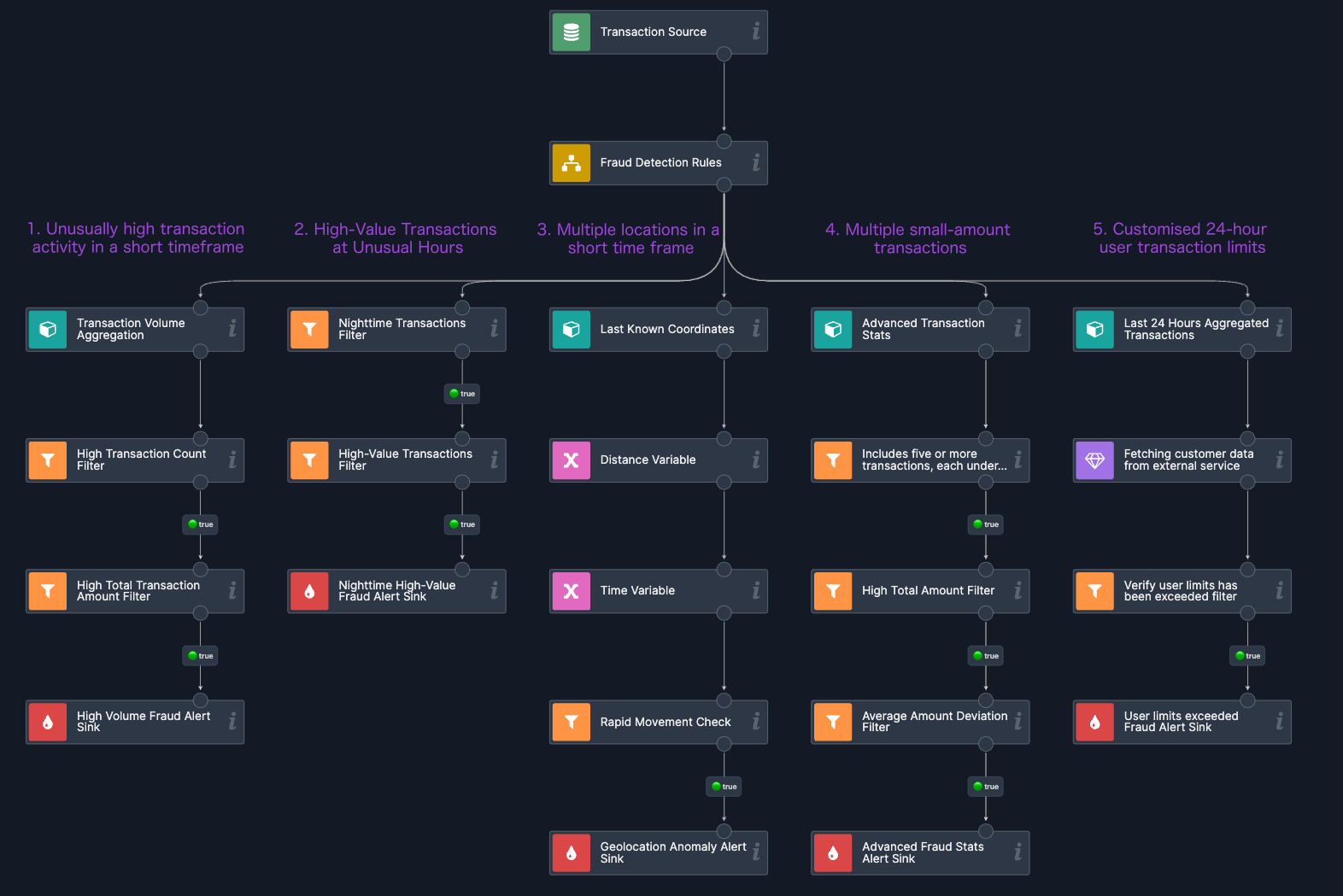
I strongly recommend you to check our live demo scenario for fraud detection. In the next sections, we will focus solely on the business logic behind identifying potential fraud. Each branch in the diagram above represents a distinct algorithm. When fraudulent activity is detected, it is published as an event to a Kafka topic. Let’s now explore our fraud detection rules in detail.
Unusually high transaction activity in a short timeframe
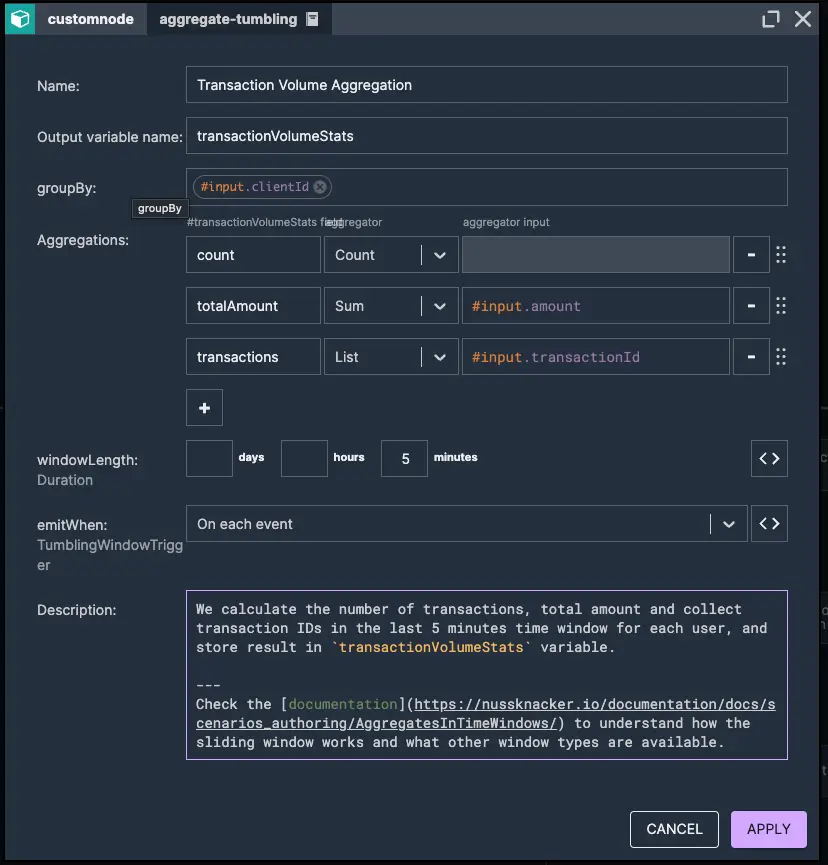
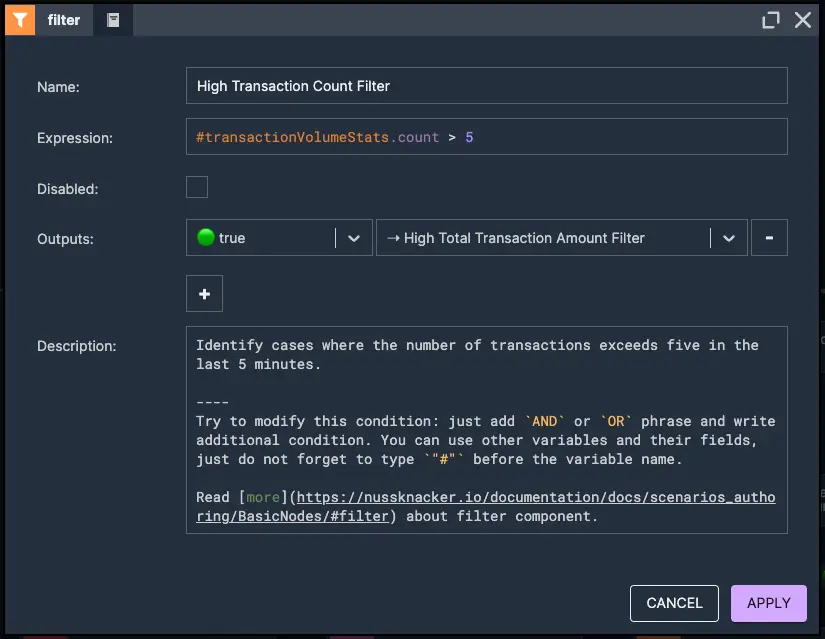
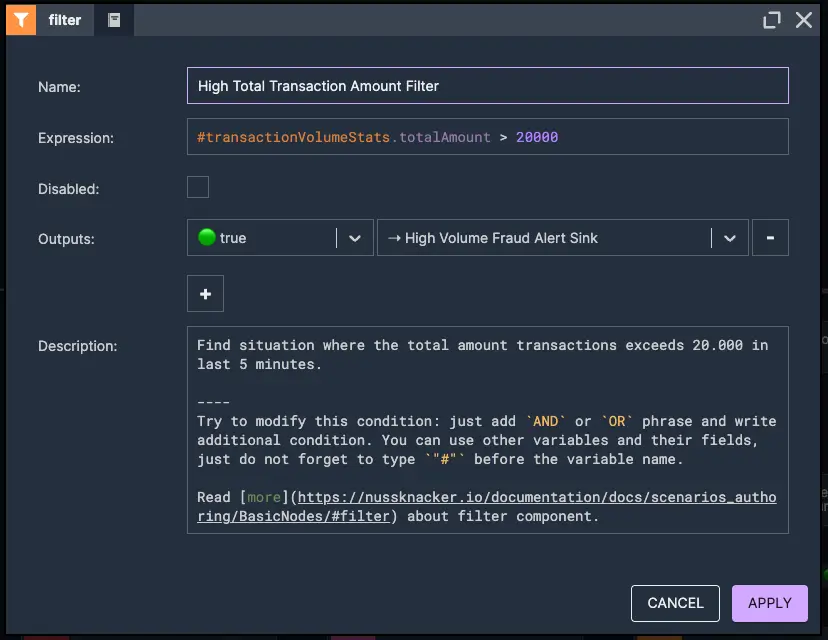
In this case, we will monitor and aggregate a user's transactions within a 5 minute time window. For each window, we will calculate both the number of transactions and the total transaction amount. The aggregation is updated and released after each new event, ensuring real-time analysis. Next, we check if the user has made more than 5 transactions or if the total transaction amount exceeds 20,000. If either condition is met, the activity is flagged as potentially fraud.
1. Transaction 5-minute time window aggregation
2. High transaction count filter
3. High total transaction amount filter
4. Push high transaction activity alarm event
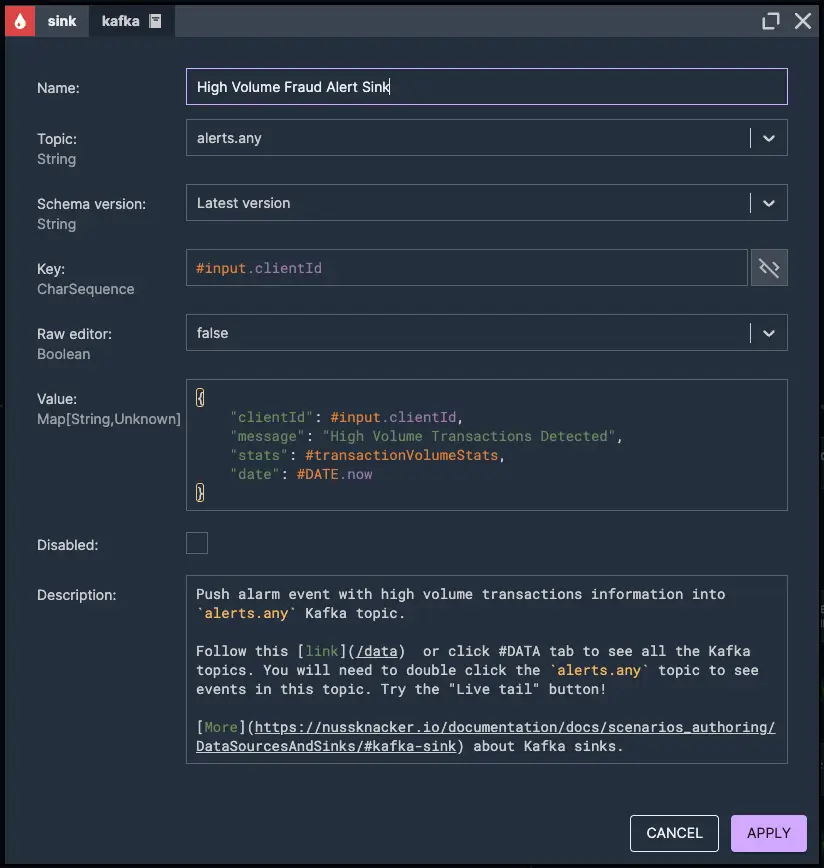
High-Value Transactions at Unusual Hours
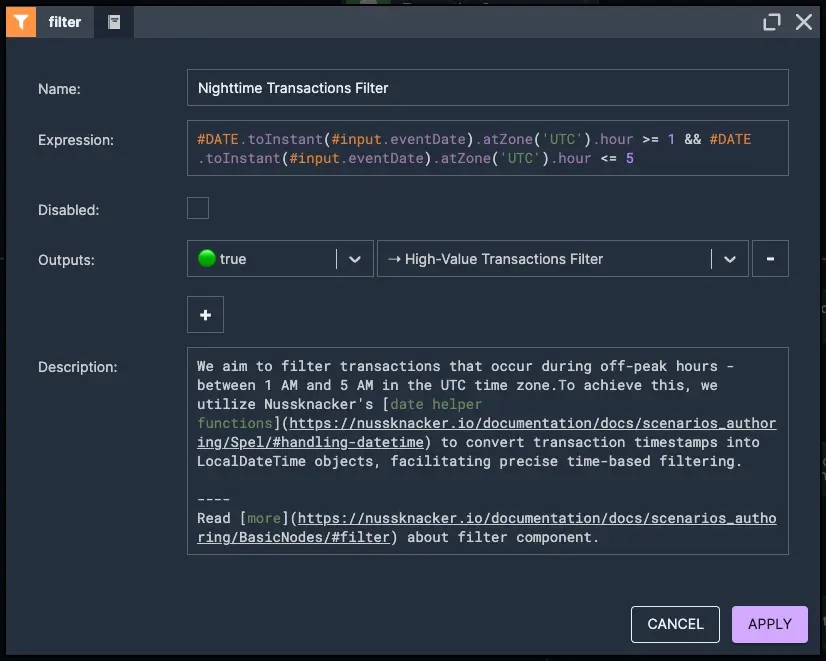
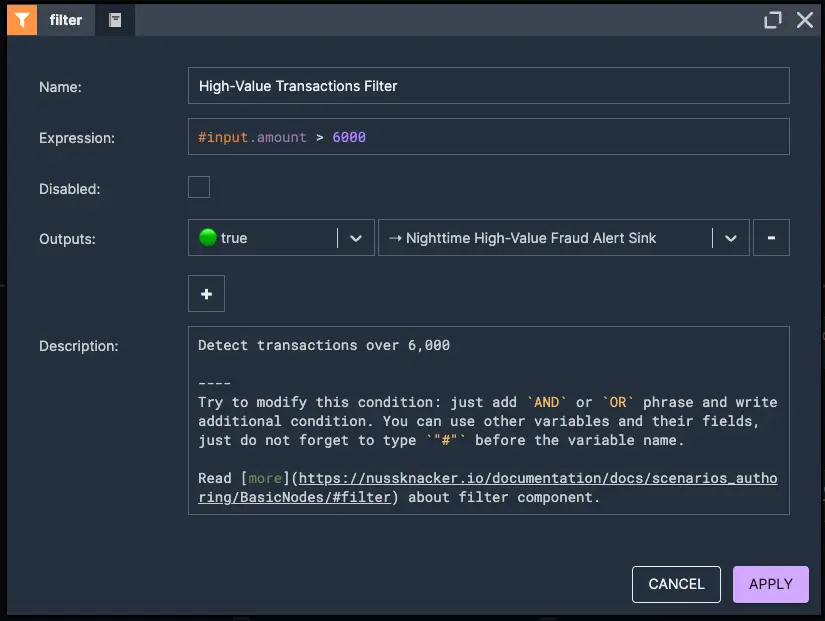
In this example, we will consider a rule that identifies unusually high-value transactions occurring during off-peak hours, a common indicator of potential fraud. Specifically, the rule flags transactions exceeding 6,000 that take place between 1 AM and 5 AM, a time window when legitimate transaction activity is typically minimal.
1. Detect transaction occurs between 1 AM and 5 AM in the UTC time zone
2. Detect transaction amount exceeds 6,000
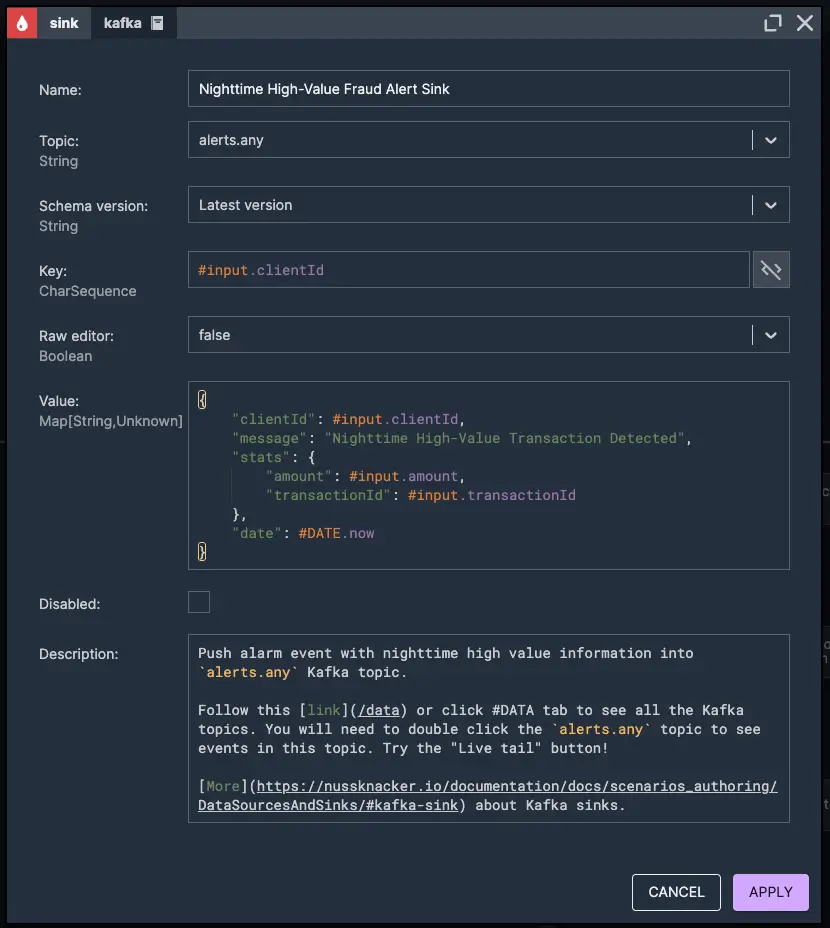
3. Push nighttime high-value transaction alarm event
Multiple locations in a short time frame
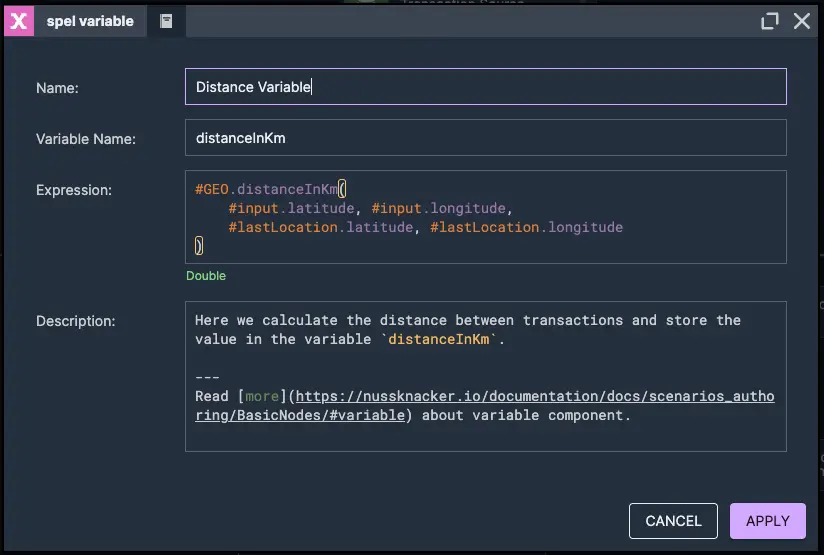
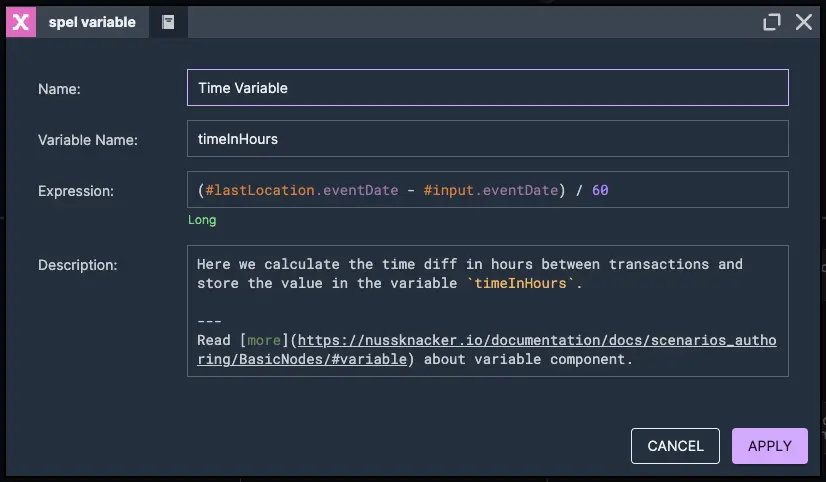
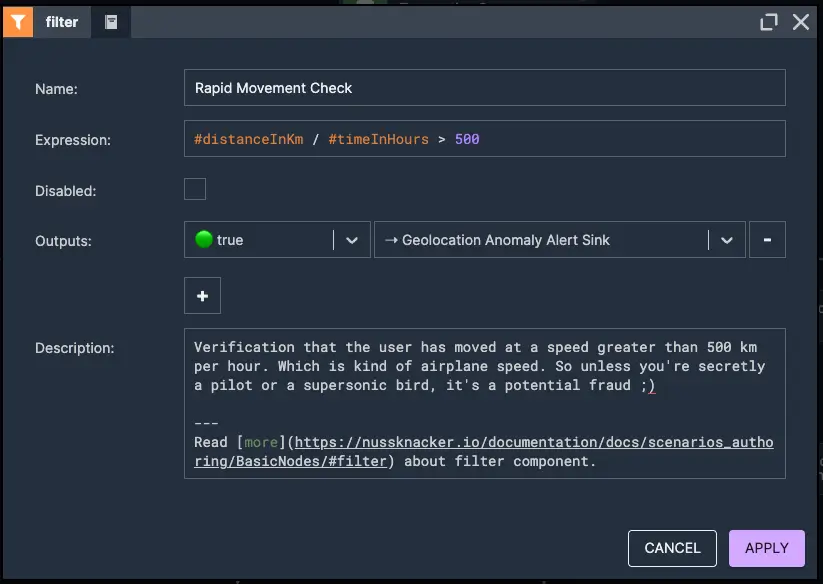
This rule detects cases where a customer is making transactions from several distant locations within a short period of time, indicating potential fraudulent activity. We calculate the distance between the last transaction and the current location, then we calculate the time between these two transactions, and finally we calculate the customer's speed and check if it's more than 500 KM per hour - basically, if they're moving at airplane speed, they might be a fraudster… or a superhero! ;)
1. Setting previous known coordinates
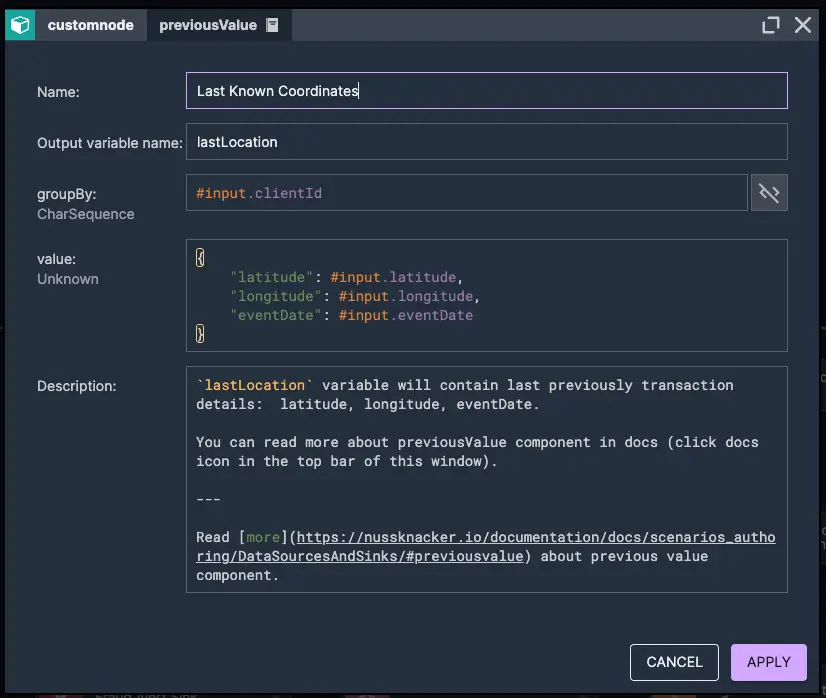
2. Calculate distance between transactions
3. Calculate time diff between transactions
4. Verify if user moved faster than 500 km / hour
5. Push geolocation anomaly alarm event
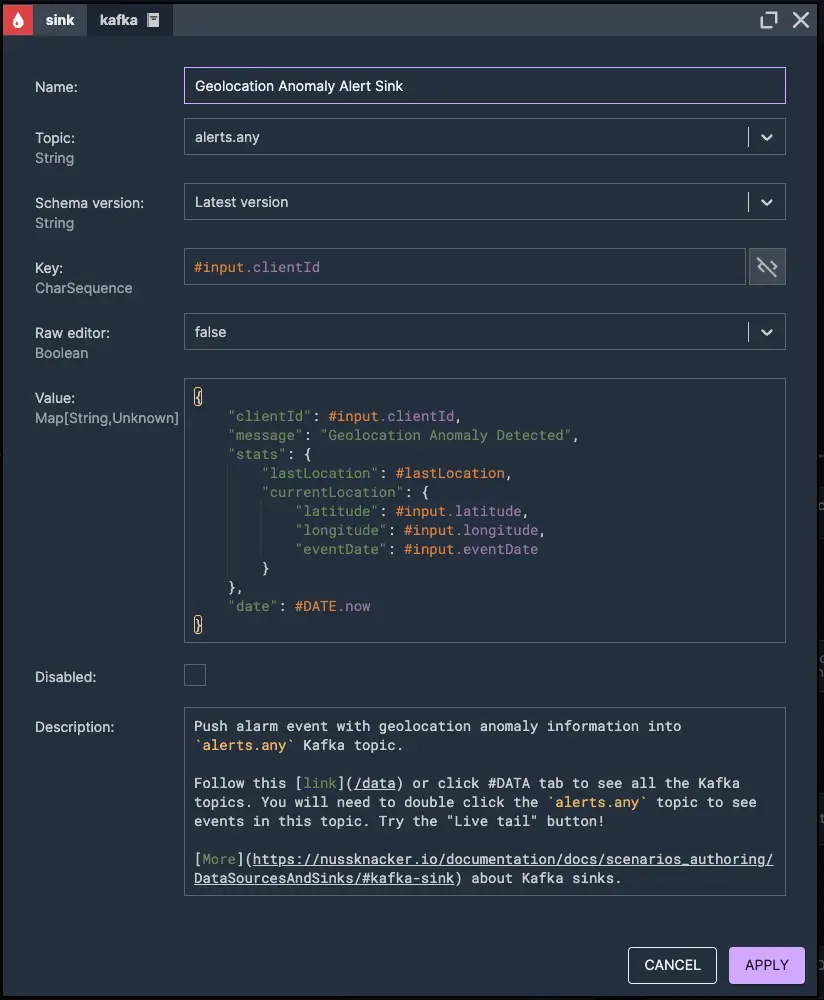
Multiple small-amount transactions
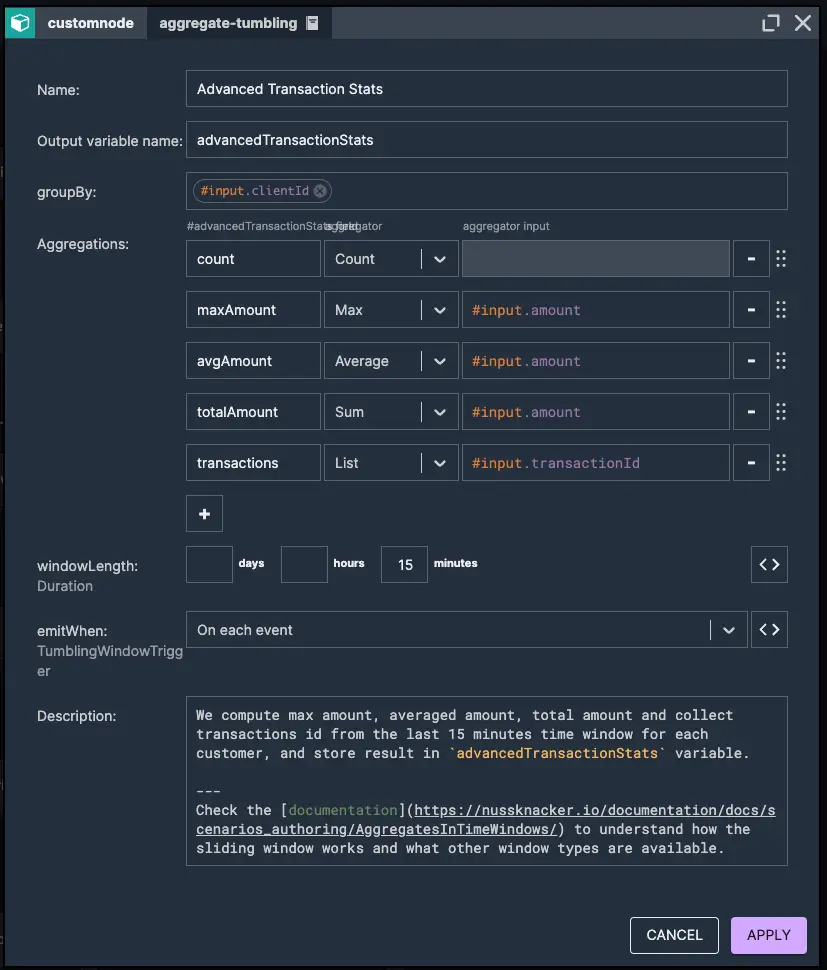
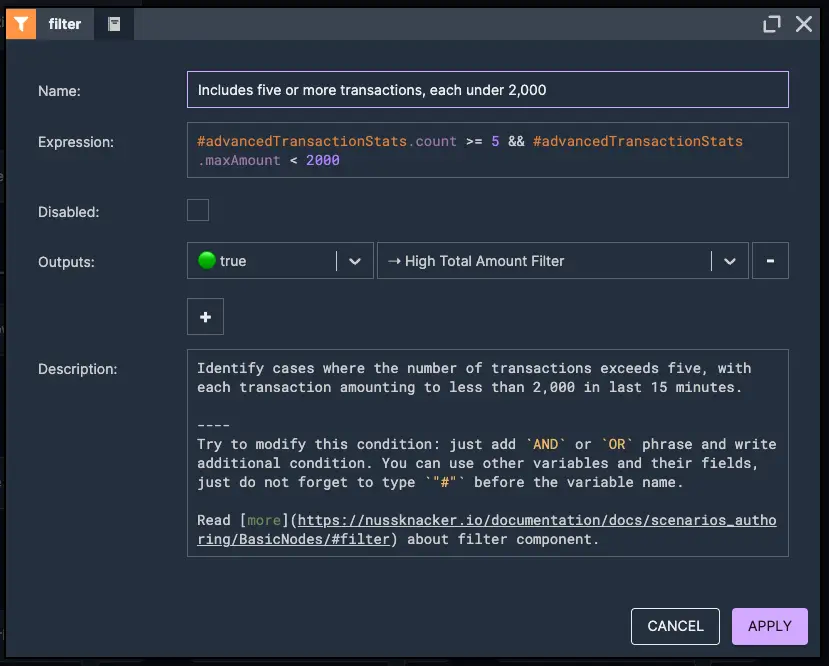
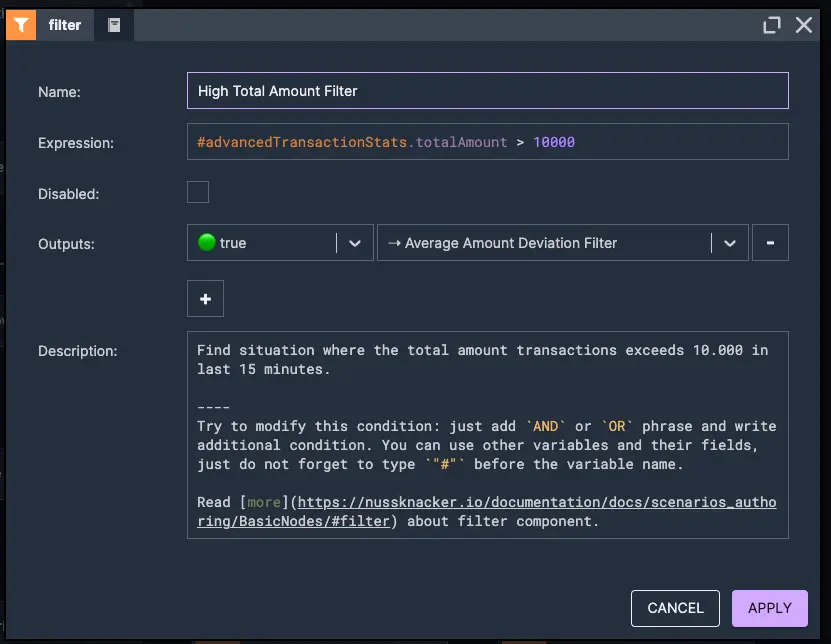
As a next scenario, we will analyze user transactions within a 15-minute time window, computing key metrics such as the maximum transaction amount, average transaction amount, total number of transactions and cumulative transaction amount. Next, we will look for suspicious behaviour by verifying if the number of transactions exceeds 5, the maximum transaction amount is less than 2,000, and the total transaction amount exceeds 10,000. Finally, we will assess whether the average transaction amount appears unusually uniform, as this could indicate an attempt to bypass detection systems by structuring transactions in a certain pattern.
1. Aggregation of transaction statistics in 15-minute time windows
2. Includes five or more transactions, each under 2,000
3. High total amount verification
4. Average amount deviation filter
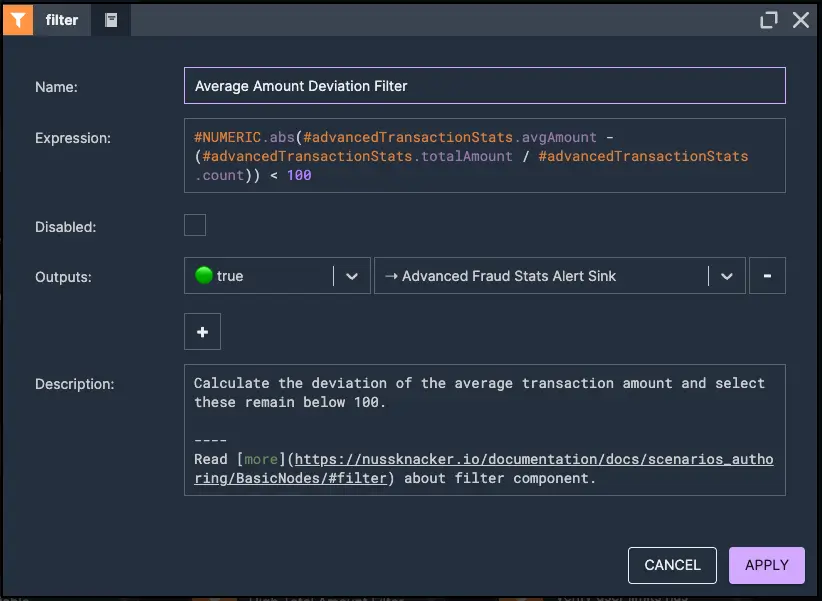
5. Push multiple transactions alarm event
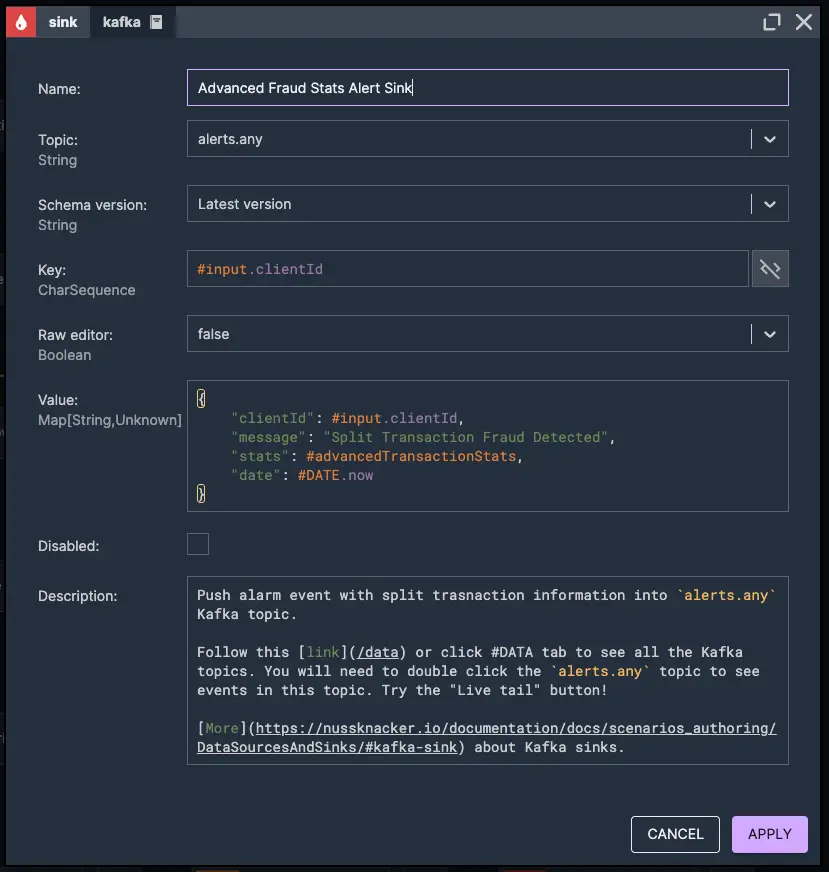
Customised 24-hour user transaction limits
This scenario is quite similar to the Unusually High Transaction Activity in a Short Timeframe fraud detection, but with a key difference, we analyze transactions over a 24-hour period instead of a short time window. Each user defines their own limits for the maximum number of transactions and the total transaction amount within this timeframe in an external system.
One important aspect of this approach is that the transaction data stream itself doesn’t contain user-specific limit configurations. To retrieve this data, we enhance our stream by connecting to an external service through OpenAPI integration, dynamically fetching each user's predefined thresholds. Finally, we verify whether any of these limits have been exceeded, flagging potential fraud cases accordingly.
1. Last 24 hours aggregated transactions stats
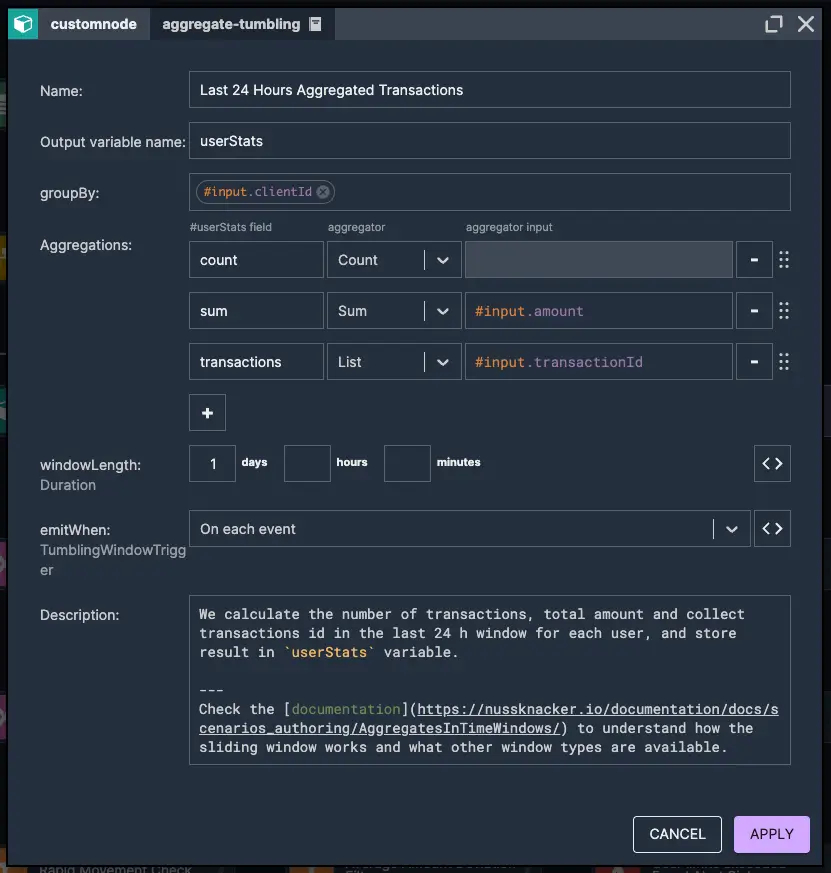
2. Fetching customer data from external service via OpenApi
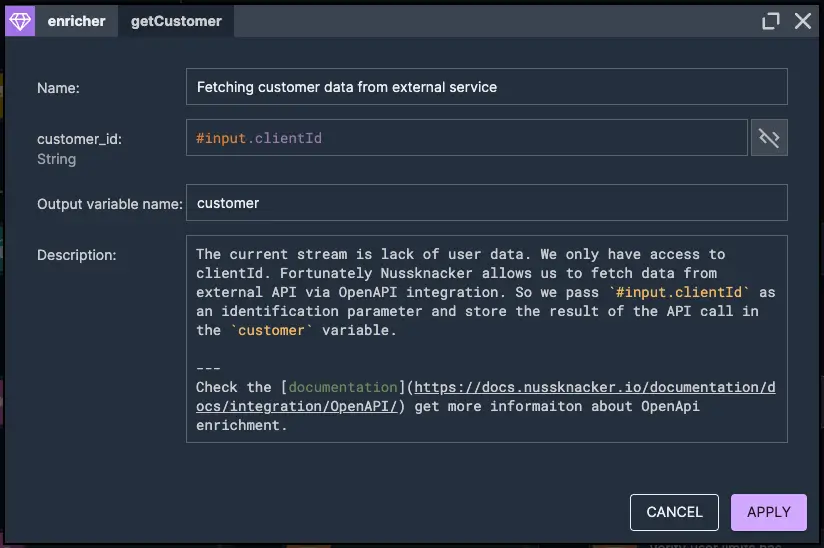
3. Verify user limits has been exceeded
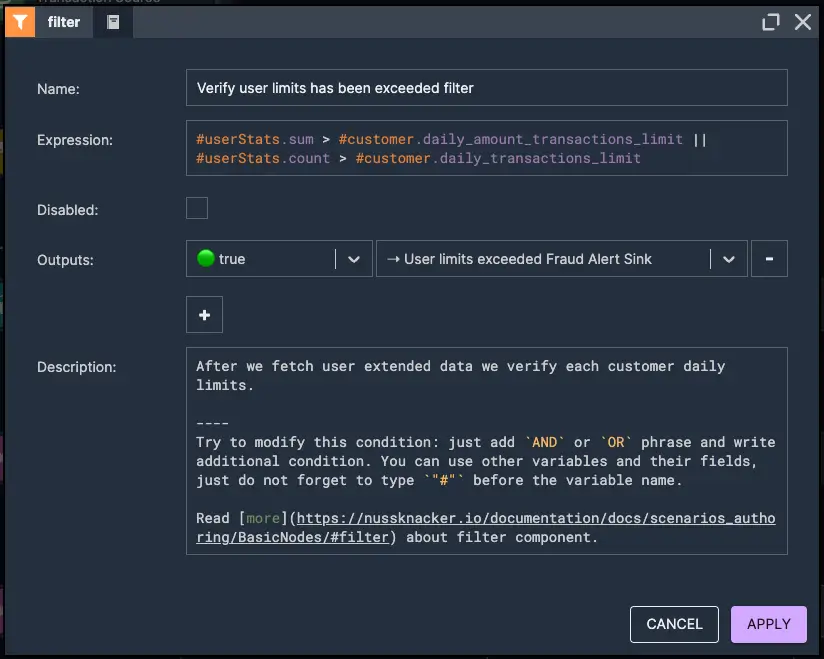
4. Push user limit exceeded alarm event
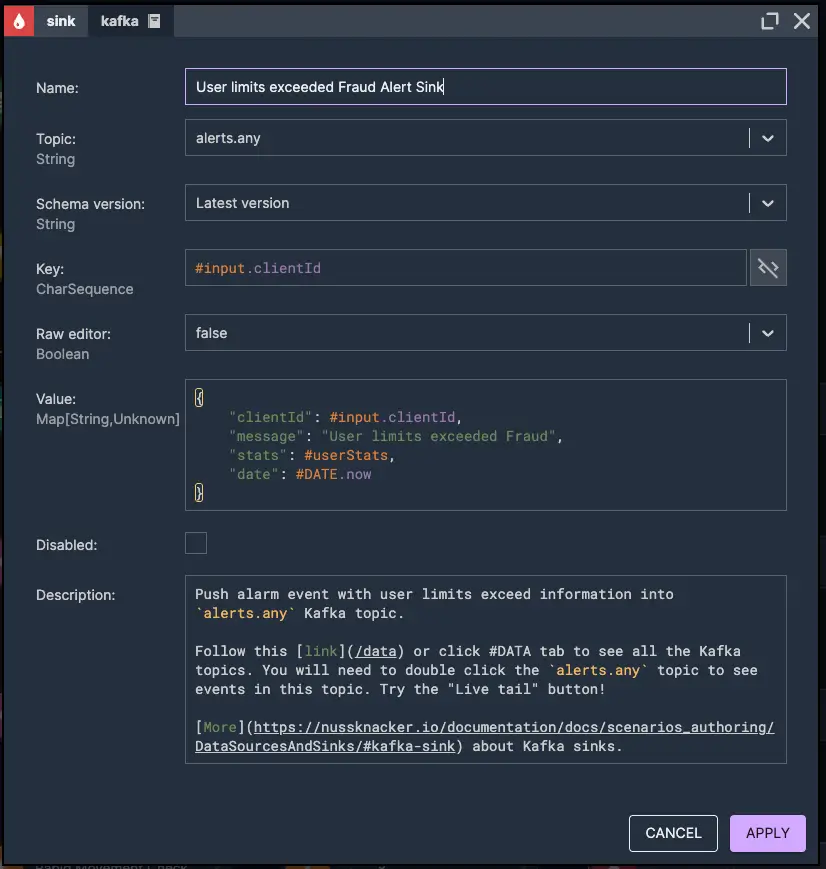
Find your own way to protect your customers
Fraud patterns are constantly evolving, making it essential for businesses to stay ahead by adapting their detection strategies. To effectively combat fraud, systems must be designed to react quickly and adjust to new threats in real time. One could extend the scenario and leverage machine learning can significantly enhance fraud detection by identifying and flagging suspicious transactions based on dynamic patterns rather than static rules. What we’ve explored so far is only a glimpse of what’s possible. With continuous innovation, businesses can develop smarter fraud detection scenarios that adapt to emerging risks and protect transactions more effectively.
More to come, stay tuned guys!
Building Iceberg Lakehouse with AWS Glue
Leverage Nussknacker to build a modern data lakehouse on S3 using Apache Iceberg and AWS Glue.
Understanding Event Time in Nussknacker
Learn why Event time is crucial in stream processing and how Nussknacker leverages it for reliable stateful computations.
Generation-Augmented Retrieval (GAR) for Product Recommendation
How to quickly launch a solution based on LLM/Foundational Models to engage customers.
Feel free to ask any questions
Nussknacker can make your data processing use case more agile and easier to manage.